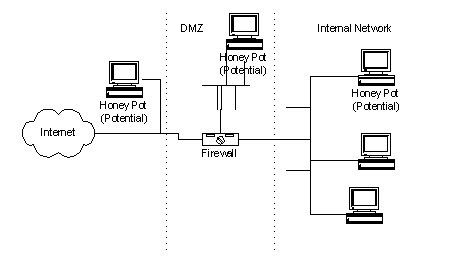
What is a Honeypot
Considering the classical field of computer security, a computer needs to be secure, but in the domain of Honeypots, the security holes are set to open on purpose. Honeypots can be defined as a trap that is set to detect attempts at any unauthorized use of information systems. Honeypots essentially turn on the tables for Hackers and computer security experts. The main purpose of a Honeypot is to detect and learn from the attacks and further use the information to improve security. Honeypots have long been used to track attackers’ activity and defend against coming threats. There are two types of honeypots:
Why set up Honeypots
The worth of a honeypot is weighed by the information that can be obtained from it. Monitoring the data that enters and leaves a honeypot lets the user gather the information that is not otherwise available. Generally, there are two popular reasons for setting up a Honeypot: Understand how hackers probe and attempt to gain access to your systems. The overall idea is that since a record of the culprit’s activities is kept, one can gain an understanding of the attack methodologies to better protect their real production systems. Gather forensic information that is needed to aid in the apprehension or prosecution of hackers. This is the sort of information that is often needed to provide law enforcement officials with the details needed to prosecute.
How Honeypots secure Computer Systems
A Honeypot is a computer connected to a network. These can be used to examine the vulnerabilities of the operating system or the network. Depending on the kind of setup, one can study security holes in general or in particular. These can be used to observe the activities of an individual who gained access to the Honeypot. Honeypots are generally based on a real server, a real operating system, along with data that looks real. One of the chief differences is the location of the machine in relation to the actual servers. The most vital activity of a honeypot is to capture the data, the ability to log, alert, and capture everything the intruder is doing. The gathered information can prove to be quite critical against the attacker.
High-Interaction vs. Low-Interaction Honeypots
High-interaction honeypots can be compromised entirely, permitting an enemy to gain full access to the system and use it to launch further network attacks. With the help of such honeypots, users can learn more about targeted attacks against their systems or even about insider attacks. In contrast, the low-interaction honeypots put on only services which cannot be exploited to get complete access to the honeypot. These are more limited but are useful for gathering information at a higher level.
Advantages of using Honeypots
Collect Real Data
While Honeypots collect a small volume of data but almost all of this data is a real attack or unauthorized activity.
Reduced False Positive
With most detection technologies (IDS, IPS) a large fraction of alerts are false warnings, while with Honeypots this doesn’t hold true.
Cost Effective
Honeypot just interacts with malicious activity and does not require high-performance resources.
Encryption
With a honeypot, it doesn’t matter if an attacker is using encryption; the activity will still be captured.
Simple
Honeypots are very simple to understand, deploy and maintain. A Honeypot is a concept and not a tool that can be simply deployed. One needs to know well in advance what they intend to learn, and then the honeypot can be customized based on their specific needs. There is some useful information on sans.org if you need to read more on the subject.